Password security tips are paramount in today’s digital landscape. Protecting your online accounts requires a multi-faceted approach encompassing strong passwords, robust management techniques, and vigilant security practices. This guide provides actionable advice to bolster your digital defenses.
From crafting complex passwords to leveraging password managers and multi-factor authentication, this comprehensive resource equips you with the knowledge to safeguard your sensitive information. Understanding common security pitfalls and best practices is crucial in this ever-evolving digital realm.
Password Complexity

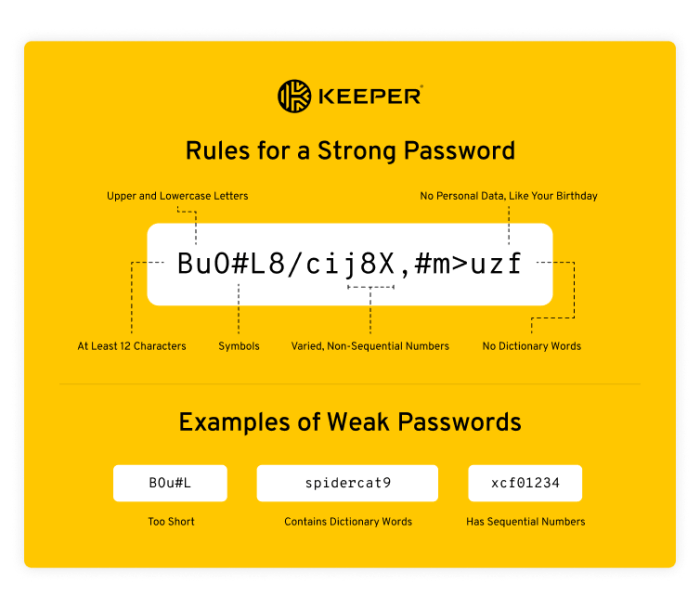
A strong password is the cornerstone of online security. Choosing robust passwords is crucial for safeguarding your accounts from unauthorized access. This section delves into the critical elements of password strength, providing practical guidance and examples to enhance your password security practices.Effective passwords are more than just a string of characters; they are carefully crafted to resist common hacking attempts.
Understanding the principles of strong passwords, from length to randomness, is paramount in today’s digital landscape. This knowledge empowers you to create passwords that are both secure and easy to remember.
Strong Password Criteria
A robust password fulfills several key criteria. Length, incorporating various character types, and randomness are essential components. A lengthy password with diverse character types and a high degree of randomness makes it extremely challenging for attackers to crack.
Password Strength Examples
The table below illustrates the varying degrees of password strength and their associated vulnerabilities.
| Password Type | Example | Vulnerability |
|---|---|---|
| Weak | 123456 | Easily guessed by brute-force attacks or dictionary attacks. Predictable and short. |
| Medium | Pa$$wOrd1 | Slightly more complex but still susceptible to attacks. Uses a mix of upper and lower case letters and numbers, but the password is short and predictable. |
| Strong | 7!@#$%^&*abcXYZ1234 | Difficult to crack due to length, mix of character types, and randomness. |
Password Generation Methods
Several methods facilitate the creation of random passwords. Employing password managers, using dedicated online password generators, or combining unique character combinations are effective approaches.
- Password Managers: Password managers generate and securely store complex passwords for you. They automatically fill in login details, reducing the risk of weak passwords. They also facilitate password management across multiple accounts, which is crucial for security.
- Online Password Generators: These tools create strong, random passwords based on specific criteria. They offer options for customizing password length and character types. Use tools that employ high-level randomness algorithms for superior security.
- Combining Character Combinations: Combining elements of your interests, such as a significant date, memorable phrase, or a combination of unique characters, can create strong and memorable passwords. Use a mix of upper and lower case letters, numbers, and symbols to increase security.
Character Types for Enhanced Strength
The inclusion of diverse character types significantly strengthens passwords. This table illustrates various character types that enhance password strength.
| Character Type | Examples |
|---|---|
| Uppercase Letters | A, B, C, … |
| Lowercase Letters | a, b, c, … |
| Numbers | 0, 1, 2, … |
| Symbols | !, @, #, $, %, … |
Assessing Password Complexity
Online tools assist in evaluating password complexity. These tools provide immediate feedback on password strength, guiding users towards creating more secure passwords.
- Online Password Strength Testers: Numerous websites offer password strength testers. These tools assess the complexity of a password, providing a rating (weak, medium, strong) and suggestions for improvement.
Password Management Techniques
Effective password management is crucial for online security. A robust strategy, combining strong passwords with secure management practices, significantly reduces the risk of account compromise. This section explores password management techniques, highlighting the benefits of password managers and multi-factor authentication.Password managers offer a significant advantage over manually managing passwords. They are designed to securely store and manage all your passwords, eliminating the need to memorize or write them down.
This automated approach minimizes the risk of password reuse and dramatically improves overall security.
Importance of Password Managers
Password managers are essential for securely storing and managing multiple passwords. They are more secure than using sticky notes or password lists because they employ robust encryption and access controls. This encryption ensures only authorized users can access your passwords. A password manager significantly reduces the risk of a breach compared to managing passwords manually, preventing exposure in case of a device compromise.
Benefits of Password Managers Over Writing Passwords Down
Manually writing passwords down poses significant security risks. It can be easily lost, stolen, or viewed by unauthorized individuals. This physical vulnerability exposes sensitive information, leading to potential account compromises. Password managers eliminate these risks by securely storing passwords and providing controlled access.
Types of Password Managers and Functionalities
Password managers vary in their functionalities. Some offer basic password storage and generation, while others provide more advanced features like secure note-taking, credit card management, and VPN access. A password manager’s capabilities often extend beyond basic password storage, enhancing overall online security and simplifying daily tasks.
Securely Setting Up a Password Manager Account
Setting up a password manager account requires careful consideration of security. Choose a reputable password manager and a strong, unique password for your manager account. Ensure the password manager uses robust encryption algorithms to protect your stored data. Follow the manager’s setup instructions diligently to configure access controls effectively.
Advantages of Multi-Factor Authentication (MFA) with Passwords
Multi-factor authentication (MFA) adds an extra layer of security to password protection. By requiring more than just a password, MFA makes it considerably more challenging for attackers to access your accounts even if they obtain your password. It significantly enhances security, making it virtually impossible to compromise your accounts without knowing the multiple authentication factors. This combination of strong passwords and MFA substantially strengthens security posture against unauthorized access.
Password Storage Security
Storing passwords securely is crucial for protecting your accounts and personal information. A robust password storage strategy is essential to mitigate the risk of unauthorized access and data breaches. This section delves into best practices for safeguarding your passwords and managing your password manager effectively.Password storage security goes beyond simply choosing strong passwords. It involves understanding the different methods used to protect your passwords and the potential risks associated with insecure practices.
This includes recognizing the importance of using a reputable password manager and understanding the security protocols employed by major online services.
Secure Password Storage Practices
Password storage security requires a multi-faceted approach. This includes using strong passwords, implementing secure storage techniques, and understanding how various services handle password management.
- Using a Reputable Password Manager: A password manager is a software application designed to securely store and manage your passwords. Choose a reputable password manager from a trusted vendor. Look for features such as two-factor authentication, encryption, and regular security audits. A robust password manager encrypts your passwords using industry-standard algorithms, protecting them from unauthorized access even if your device is compromised.
- Strong Password Management Practices: Implementing secure password management practices is key to minimizing risks. Utilize strong passwords for all accounts and avoid reusing passwords across different platforms. Avoid storing passwords in plain text files, or even in easily accessible documents on your computer. Password managers provide a secure and organized method for storing your passwords. This ensures only authorized users can access your credentials.
- Multi-Factor Authentication (MFA): Employing MFA adds an extra layer of security to your password manager and accounts. This involves using multiple verification methods, such as a code sent to your phone or a security token, in addition to your password. This significantly reduces the risk of unauthorized access, even if someone gains access to your password.
Protecting Your Password Manager
Protecting your password manager from unauthorized access is critical. A compromised password manager could expose all your sensitive login credentials.
- Strong Password for Password Manager: Choose a unique and complex password specifically for your password manager. This password should be different from all other passwords you use. This prevents unauthorized access to your password manager if it is compromised.
- Strong Device Security: Ensure your devices, including your computer and mobile phone, are protected with strong passwords, anti-virus software, and regular updates. This prevents unauthorized access to your password manager, which could expose all stored passwords. Enable two-factor authentication wherever possible.
- Regular Password Manager Updates: Regularly update your password manager software to ensure you have the latest security patches. This helps mitigate potential vulnerabilities that attackers might exploit. Vulnerabilities can be exploited by malicious actors if not addressed promptly.
Password Storage Security on Various Devices
Protecting your passwords across different devices is crucial. The methods for securing passwords on various devices vary, but the underlying principle remains the same: employing robust security measures.
- Mobile Devices: Secure your mobile devices with strong passwords, enable two-factor authentication, and regularly update the operating system and applications. Avoid leaving your mobile devices unattended in public places. Consider using a virtual private network (VPN) when connecting to public Wi-Fi networks. These networks are often vulnerable to interception.
- Desktop Computers: Use strong passwords and enable robust security features on your desktop computer, including anti-virus software and regular updates. Ensure the operating system and applications are up to date to protect against potential vulnerabilities. Regularly review your desktop computer’s security settings.
- Cloud Storage: Choose reputable cloud storage services that employ strong encryption protocols. Be mindful of the security settings and access controls associated with your cloud storage accounts. Using robust cloud storage services ensures data integrity and confidentiality.
Password Storage Security Protocols of Major Websites and Services
Major websites and services employ various security protocols to protect user passwords. These protocols often involve encryption, hashing, and multi-factor authentication.
- Encryption: Most major websites and services utilize encryption to protect user data during transmission. This ensures that your password is not readable by unauthorized parties during transit. This method protects against data breaches during transmission.
- Hashing: Password hashing is a one-way function that transforms passwords into a unique string. This makes it extremely difficult to reverse the process and recover the original password. This protects against unauthorized access by preventing decryption of passwords.
- Multi-Factor Authentication (MFA): Many reputable websites and services offer MFA to add an extra layer of security. This involves requiring additional verification steps beyond a password, such as a code sent to a mobile phone or a security token. This prevents unauthorized access by requiring more than one form of verification.
Dangers of Storing Passwords in Plain Text
Storing passwords in plain text is extremely risky and should be avoided. This practice exposes your passwords to unauthorized access and potential data breaches.
- Risk of Data Breaches: If a system containing plain-text passwords is compromised, all the stored passwords become immediately vulnerable. This makes all accounts using those passwords susceptible to unauthorized access.
- Unauthorized Access: Plain-text passwords are easily accessible to anyone who gains unauthorized access to the storage location. This includes malicious actors who could potentially exploit vulnerabilities in a system to access stored data.
- Identity Theft: Stolen passwords can be used to access other accounts, leading to identity theft and financial loss. This includes unauthorized access to financial accounts, credit cards, and other sensitive information.
Password Recovery and Reset Procedures
Password recovery and reset procedures are crucial components of a robust password security strategy. A well-defined process allows users to regain access to their accounts without compromising their data. This section details the steps involved, highlighting the importance of security measures and best practices.Effective password recovery and reset processes are essential for maintaining account security. Users must be able to regain access to their accounts quickly and securely without compromising personal information or potentially exposing accounts to unauthorized access.
Strong passwords are crucial, but modern security is evolving. Machine learning applications are increasingly used to detect and prevent cyber threats, like identifying unusual login patterns. This highlights the ongoing need for robust password security measures, and a need for continuous learning and adaptation in the field. Ultimately, safeguarding your accounts relies on a blend of traditional security practices and the latest innovations.
Password Recovery Steps
A well-defined password recovery process should include several key steps. Users should be guided through a series of verification procedures to ensure that the account is being accessed by the rightful owner. These steps often involve a combination of questions, security tokens, and other authentication methods.
- Verification Request: The user initiates the password recovery process by requesting a password reset. This typically involves providing identifying information, such as an email address or phone number associated with the account.
- Security Question Verification: Many platforms utilize security questions to verify the user’s identity. The user must answer these pre-defined questions accurately. These questions should be unique and challenging to guess, preventing unauthorized access.
- Alternative Authentication: In addition to security questions, some platforms may utilize alternative authentication methods, such as a one-time code sent to a registered mobile phone or email address. This provides an additional layer of security.
- Password Reset: Once the user’s identity is verified, they can proceed to reset their password to a more secure and complex one.
Secure Password Reset
Implementing secure password reset procedures is paramount to preventing unauthorized access. Strong password policies should be enforced to prevent brute-force attacks. Users should be encouraged to choose complex passwords that are difficult to guess.
- Password Complexity: Enforce password complexity requirements. These include minimum length, character types (uppercase, lowercase, numbers, symbols), and avoid common or easily guessable passwords. For example, passwords like “password123” or “qwerty” are easily cracked and should be avoided.
- Multi-Factor Authentication (MFA): Employ MFA wherever possible. MFA adds an extra layer of security, requiring more than one form of verification (e.g., username/password plus a code from a mobile app or security key).
- Account Monitoring: Continuously monitor accounts for suspicious activity. If any unusual login attempts or other security breaches are detected, the account should be locked down and the user notified immediately.
Password Recovery with Password Managers
Password managers streamline the password recovery process. They store passwords securely and often provide recovery options if a user forgets a password.
- Backup Codes: Many password managers provide backup codes or recovery options in case of account compromise. These codes can be used to recover access to the account even if the user loses access to their primary login details.
- Import/Export Functionality: Password managers allow importing and exporting password databases, enabling users to switch password managers or to have a backup copy of their credentials.
- Automated Password Reset: The password manager can automate the password reset process when necessary, providing a secure and user-friendly way to retrieve access to accounts.
Strong Recovery Questions
Strong recovery questions are critical to preventing unauthorized access. These questions should be unique and personal, difficult to guess or answer.
- Unique and Personal: Questions should be specific to the user, such as “What is the name of your first pet?” or “What is your mother’s maiden name?”.
- Difficult to Guess: Questions should not be easily found online or through public information.
- Security Considerations: Never use easily guessed or publicly available information, like the user’s current address or birth date.
Password Recovery Options
The table below Artikels various password recovery options for different platforms.
| Platform | Password Recovery Options |
|---|---|
| Social Media | Security questions, email/phone verification, MFA |
| Online Banking | Security questions, one-time codes, MFA, security keys |
| Email Accounts | Security questions, email/phone verification, account recovery emails |
| Password Managers | Backup codes, MFA, email/phone verification |
Password Usage Best Practices
Proper password usage is paramount to online security. This involves more than just creating strong passwords; it encompasses how you apply and manage those passwords across various platforms. Understanding common mistakes and adhering to best practices is crucial to safeguarding your accounts from unauthorized access.Password security isn’t a one-time effort; it’s an ongoing commitment. Consistent vigilance and a proactive approach are key to maintaining a strong security posture.
This section details best practices to enhance your password security, ensuring a more robust defense against potential threats.
Common Password Security Mistakes
Many individuals unknowingly fall prey to common pitfalls that compromise their online security. Recognizing these errors is the first step towards avoiding them.
- Reusing passwords across multiple accounts.
- Creating weak or easily guessed passwords.
- Not changing passwords frequently enough.
- Writing down passwords or storing them in insecure locations.
- Using easily identifiable information in passwords.
Creating Unique Passwords for Different Accounts
A critical aspect of robust password security is creating unique passwords for each online account. This significantly reduces the impact of a breach on any one platform.Creating a unique password for every online account is essential to mitigating the risks associated with password reuse. This practice limits the potential damage if one account is compromised. Consider using a password manager for generating and storing these unique passwords.
Avoiding Password Reuse Across Multiple Platforms
Reusing passwords across multiple accounts is a significant security vulnerability. A breach on one platform can potentially compromise access to other accounts using the same password.Avoid reusing passwords across different accounts. If a hacker gains access to one account with a reused password, they can potentially access other accounts. A unique password for each platform is a fundamental security practice.
Regular Password Changes, Password security tips
Regular password changes are vital for maintaining account security. This proactive measure minimizes the risk of unauthorized access if a password is compromised.Regular password changes significantly enhance your online security. This preventative measure is particularly crucial in situations involving data breaches or suspicious account activity. Consider setting automatic password change reminders or using password managers that automatically update passwords.
Situations Requiring Password Changes
Certain events warrant immediate password changes to maintain security. This includes compromised accounts, suspicious activity, and updates to account security settings.
- Data breaches: If a company you use has a data breach involving passwords, immediately change all passwords associated with that company.
- Suspicious activity: If you notice unusual or unauthorized login attempts on any of your accounts, immediately change the passwords to prevent further unauthorized access.
- Account security updates: Some platforms may require password changes following security updates to ensure compatibility and strengthen security protocols.
Password Policies and Guidelines
A robust password policy is crucial for any organization aiming to protect sensitive data. A well-defined policy acts as a cornerstone for safeguarding user accounts and preventing unauthorized access. It establishes clear expectations for password strength, complexity, and usage, thus reducing the risk of breaches and maintaining data integrity.Implementing a comprehensive password policy necessitates a multi-faceted approach, encompassing user education, regular security audits, and ongoing review.
This ensures that the policy remains effective and aligns with evolving security threats.
Establishing Password Policy Standards
A strong password policy sets the standards for acceptable password practices within an organization. This includes criteria for password length, complexity, and acceptable characters. These standards are designed to mitigate the risk of weak passwords, increasing the overall security posture of the system. Organizations should regularly review and update these standards to adapt to evolving security threats.
Implementing a Strong Password Policy
Implementing a strong password policy requires a structured approach. First, the organization should clearly define the policy, outlining password requirements. This includes minimum length, character types (uppercase, lowercase, numbers, symbols), and restrictions on the use of personal information. Second, users need to be educated on the policy. Third, regular security audits and reviews should be conducted to ensure compliance and identify potential weaknesses.
Educating Users on Password Security
User education is paramount in implementing a strong password policy. Training programs should cover best practices for creating strong passwords, including the use of unique passwords for different accounts. This should include demonstrations on password managers, and the importance of avoiding easily guessed passwords. Regular reminders and updates about the importance of password security are also crucial.
Conducting Regular Security Audits
Regular security audits related to passwords are essential for maintaining a strong security posture. These audits should evaluate user compliance with the password policy, identify potential vulnerabilities, and assess the effectiveness of the implemented security measures. This involves examining password history, identifying potential patterns, and checking for any unusual login attempts.
User-Friendly Password Policy Guidelines
To ensure effective user adoption of the policy, it should be presented in a clear and concise manner. A well-organized document, or a readily accessible online resource, detailing the policy requirements is essential. It should be easy to understand and follow, allowing users to readily grasp the expectations.
| Policy Element | Description | Example |
|---|---|---|
| Password Length | Minimum length of the password. | At least 12 characters. |
| Character Types | Required character types (uppercase, lowercase, numbers, symbols). | Must contain at least one uppercase letter, one lowercase letter, one number, and one symbol. |
| Password History | Restriction on repeating previous passwords. | Cannot reuse a password used in the last 3 months. |
| Password Expiration | Frequency of password changes. | Passwords must be changed every 90 days. |
Password policies should be reviewed and updated regularly to adapt to evolving security threats. Keeping pace with emerging password cracking techniques and the constant evolution of malicious actors is critical.
Phishing and Password Attacks
Protecting your passwords from cybercriminals is crucial in today’s digital landscape. A significant threat to password security is phishing, a deceptive practice used to trick individuals into revealing sensitive information, including passwords. Understanding the tactics employed by phishers and the signs of a potential scam is vital for safeguarding your accounts.Phishing attacks are often disguised as legitimate communications, making them difficult to detect.
They leverage social engineering techniques to exploit human vulnerabilities, aiming to gain access to your accounts and valuable data. Recognizing these attempts is essential to avoid becoming a victim.
Common Phishing Tactics
Phishing attacks employ various methods to target individuals. These include emails that appear to come from trusted sources, such as banks or social media platforms. These emails often contain urgent requests for information, such as account verification or password changes. Fake websites mimicking legitimate platforms are also common, designed to collect login credentials.
Recognizing and Avoiding Phishing Scams
Identifying phishing attempts requires vigilance and a discerning eye. Be wary of emails with suspicious links or attachments, especially those requesting personal information. Pay close attention to the sender’s email address; look for inconsistencies or unusual formatting. Verify any suspicious links or requests by directly visiting the legitimate website or contacting the purported institution via a known, verified channel.
Strong passwords are crucial, but as AI trends 2025 like this one develop, we need to adapt. Multi-factor authentication and regular password changes are still vital security measures. Staying informed about emerging threats is key to keeping your accounts safe.
Examples of Malicious Emails and Websites
Phishing emails often mimic official communications. For example, an email might claim to be from your bank, urgently requesting your account details. Malicious websites may mirror the design of a legitimate platform, such as an online retailer or social media site. These fraudulent sites are often subtle variations of the originals, with subtle but crucial differences. A carefully scrutinized URL is vital in verifying legitimacy.
Importance of Skepticism Regarding Unsolicited Password Requests
Never provide your password in response to unsolicited requests. Legitimate organizations will never ask for your password via email or text message. If you receive such a request, immediately report it to the relevant authorities or the platform in question.
Reporting Suspected Phishing Attempts
Reporting suspected phishing attempts is critical in combating these cyber threats. Report suspicious emails or websites to the relevant authorities, such as your Internet Service Provider (ISP) or the platform targeted by the attack. Many platforms have specific reporting mechanisms to help identify and block fraudulent activity. Providing details about the suspicious email or website will assist in the investigation.
Also, notify the affected platform or institution.
Protecting Accounts from Brute-Force Attacks
Brute-force attacks are a significant threat to online accounts. These attacks rely on systematically trying numerous password combinations until a correct one is found. Understanding how these attacks work and implementing preventative measures is crucial for safeguarding your digital presence.A brute-force attack exploits the vulnerability of easily guessable passwords or weak security measures. The attacker employs automated tools to rapidly generate and test numerous password possibilities.
These tools can systematically try variations of common passwords, dictionary words, and even random character combinations. The success of a brute-force attack hinges on the time it takes to find the correct password and the lack of preventative measures on the target system.
How Brute-Force Attacks Work
Brute-force attacks work by systematically trying every possible password combination until the correct one is found. Attackers use automated tools that can generate and test millions of passwords per second. The tools may use common passwords, dictionary words, or randomly generated sequences. The effectiveness of this method depends on the length and complexity of the password, as well as the target system’s defenses.
This is why strong, unique passwords are essential.
Preventing Brute-Force Attacks on Your Accounts
Implementing strong passwords, enabling two-factor authentication (2FA), and utilizing password managers are effective preventative measures.
- Strong Passwords: Creating strong, unique passwords for each account is paramount. Avoid using easily guessable information, such as birthdays, names, or common phrases. Employ a combination of uppercase and lowercase letters, numbers, and symbols. Longer passwords are more resistant to brute-force attacks.
- Two-Factor Authentication (2FA): Activating 2FA adds an extra layer of security. This requires a secondary verification method, such as a code sent to your phone, in addition to your password. This makes it significantly harder for attackers to gain access even if they manage to guess your password.
- Password Managers: Password managers generate and store strong, unique passwords for all your accounts. They also securely manage your login information, eliminating the need to remember numerous complex passwords.
Security Measures Websites Can Use
Websites can implement various security measures to protect against brute-force attacks.
- Account Lockout Policies: Account lockout policies temporarily block access to an account after a predetermined number of failed login attempts. This temporarily mitigates the impact of brute-force attacks by halting automated attempts. These policies can be configured to prevent repeated attacks.
- Rate Limiting: Rate limiting restricts the frequency of login attempts. This technique slows down the rate at which attackers can try different passwords. It is implemented by the websites to control automated attacks.
- Captcha and Security Questions: Implementing CAPTCHA and security questions adds an extra layer of security, making it more difficult for automated tools to access accounts. These measures can help identify and block automated attacks.
The Role of Account Lockout Policies
Account lockout policies help mitigate brute-force attacks by temporarily suspending access to an account after a specified number of failed login attempts. This temporary suspension hinders attackers from repeatedly trying passwords, making the account less vulnerable.
Importance of Account Security Settings
Account security settings, such as two-factor authentication, password complexity requirements, and account lockout policies, are critical in preventing unauthorized access. These settings contribute to a layered approach to security, making it significantly harder for attackers to compromise accounts. Implementing robust security settings strengthens the overall security posture of the system.
Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is a crucial security measure that adds an extra layer of protection beyond a simple password. By requiring multiple forms of verification, MFA significantly reduces the risk of unauthorized access to accounts, even if a password is compromised. This enhanced security is vital in today’s digital landscape, where online accounts hold significant personal and financial information.MFA works by demanding verification from multiple sources, essentially requiring users to prove they are who they claim to be.
This process strengthens security by requiring more than just a single point of failure, like a password. The addition of these verification steps significantly hinders malicious actors who might attempt to gain access to accounts.
Advantages of MFA
MFA significantly improves account security by making it harder for attackers to access accounts even if they obtain a password. This is because multiple factors of verification are required, making it more challenging for an attacker to successfully impersonate a legitimate user. The protection afforded by MFA is often more effective than password security alone.
Types of MFA Methods
Various methods are available for MFA, each with varying degrees of security and convenience. These methods can be broadly categorized as something you know (password), something you have (phone), and something you are (biometric).
- SMS-based MFA: This method sends a one-time code via text message to the user’s registered phone number. This method is widely used and often readily available, but it can be vulnerable to SIM swapping attacks where attackers take control of a user’s phone number.
- Authenticator Apps (e.g., Google Authenticator, Authy): These apps generate time-based one-time passwords (TOTPs). They are generally considered more secure than SMS-based MFA as they don’t rely on SMS infrastructure. These apps use cryptographic techniques to generate unique codes, adding a layer of protection against interception.
- Biometric Authentication (e.g., fingerprint, facial recognition): This method uses unique physical characteristics to verify identity. Biometric authentication is generally highly secure, as it’s difficult to replicate a user’s unique biological traits. However, the technology and infrastructure for implementing it can be more complex.
- Hardware Tokens: These physical devices generate one-time passwords. They are considered highly secure due to their physical nature, making them less susceptible to hacking. They offer a robust alternative to software-based authentication.
Setting Up MFA on Various Platforms
The process of setting up MFA varies depending on the platform. Generally, users will need to navigate to the security settings of the platform’s account and enable MFA. Specific instructions for setting up MFA on various platforms can often be found on the platform’s help center.
- Identify the MFA option: Locate the security settings on the platform. Look for an option specifically labeled “Multi-Factor Authentication,” “Two-Factor Authentication,” or similar terminology.
- Choose the method: Select the MFA method that best suits your needs and security preferences. Consider the security strength and ease of use of the various options.
- Follow the instructions: The platform will provide step-by-step instructions to complete the setup process. This typically involves linking a secondary device or providing personal information for verification.
Comparing and Contrasting MFA Options
The security level of different MFA methods varies. SMS-based MFA is generally less secure than authenticator apps or hardware tokens due to the vulnerability of SMS channels. Biometric authentication, while highly secure, requires specialized infrastructure. The choice of method should be based on the level of security required and the resources available.
| Method | Security Level | Ease of Use |
|---|---|---|
| SMS | Moderate | High |
| Authenticator App | High | Moderate |
| Biometric | Very High | High |
| Hardware Token | Very High | Moderate |
Importance of Choosing Strong MFA Factors
Selecting a strong MFA factor is critical to the overall security of your accounts. The stronger the factor, the harder it is for attackers to gain unauthorized access. A weak factor could potentially compromise your account security. Choosing the appropriate method ensures a strong level of security.
Password Security for Children and Adolescents: Password Security Tips
Protecting children’s online accounts requires a multifaceted approach that combines strong password practices with robust safety education. A child’s digital footprint starts early, and establishing good habits now will benefit them throughout their lives. This involves not just choosing strong passwords, but also understanding the risks associated with online interactions and the importance of responsible digital citizenship.
Designing Secure Passwords for Children
Creating strong passwords for children and adolescents requires a balance between security and memorability. Children should be encouraged to use a mix of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable information like their name, birthday, or pet’s name. Consider using a password manager for children if they are old enough to understand the concept and use it correctly.
Educating Children About Online Safety and Passwords
Children need to understand the importance of keeping their passwords secret. Explain that passwords are like keys to their accounts and should never be shared with anyone. Use age-appropriate language to explain the risks of phishing attempts, social engineering, and other online threats. Teaching them to be cautious about clicking links or downloading files from unknown sources is also crucial.
Visual aids and interactive games can make these concepts more engaging and memorable.
Parental Controls and Account Protection
Parental controls can play a significant role in safeguarding children’s accounts. These controls often allow parents to monitor online activity, set time limits, and filter inappropriate content. Properly configured parental controls can help limit exposure to potential dangers. It is important to understand the specific controls available within each platform or device. Parents should familiarize themselves with the settings to ensure appropriate levels of security and access.
Regular Conversations About Online Safety
Regular conversations about online safety are essential for fostering responsible digital citizenship. Open communication helps children understand the potential risks and how to respond appropriately. Use these discussions as opportunities to address password security, online privacy, and cyberbullying. Parents should be proactive in asking questions and listening to their children’s concerns. This dialogue builds trust and equips children with the knowledge to navigate the digital world safely.
Resources for Parents
Numerous resources can support parents in discussing password security with their children. Many websites and organizations offer educational materials, tips, and guidelines on online safety. Consult the resources provided by your internet service provider, schools, or community organizations. Utilizing these resources can ensure children are well-equipped to handle the digital world responsibly.
Hardware Security Modules (HSM)
Hardware Security Modules (HSMs) are specialized, dedicated hardware devices designed to enhance the security of sensitive data, including passwords. They are crucial for organizations handling confidential information and maintaining robust security posture. Their physical isolation and cryptographic capabilities make them a strong bulwark against various threats.HSMs act as trusted intermediaries for cryptographic operations. They securely store and manage cryptographic keys, preventing unauthorized access and use.
This approach strengthens overall password security by limiting potential points of compromise. Their inherent security features protect sensitive data from breaches, ensuring that passwords remain confidential and usable within a controlled environment.
How HSMs Secure Passwords
HSMs provide a secure environment for managing cryptographic keys used in password hashing and encryption. They isolate these keys from the operating system and other applications, significantly reducing the risk of compromise. By handling cryptographic operations within the HSM’s isolated environment, the risk of malicious code accessing and modifying password information is minimized.
Role in Protecting Sensitive Data
HSMs play a vital role in protecting sensitive data by securely storing and managing cryptographic keys. This secure storage and management process is critical for ensuring data integrity and confidentiality. The inherent security of HSMs helps organizations comply with regulatory requirements for data protection. These modules offer a robust defense against unauthorized access to sensitive data, including passwords.
Basic Overview of HSM Functionality
HSMs function as dedicated cryptographic engines. They are physically isolated from the rest of the system, reducing the risk of malicious code compromising the cryptographic keys. The HSM’s dedicated hardware architecture and cryptographic algorithms provide a strong security foundation. The HSM’s internal processes are designed to prevent unauthorized access to its internal components and cryptographic keys. This isolation ensures that only authorized personnel and processes can interact with the HSM.
Improving Overall Password Security
HSMs contribute to improved password security by securely managing the cryptographic keys used for password hashing and encryption. This secure key management eliminates the vulnerabilities associated with storing passwords in cleartext or poorly protected environments. The dedicated hardware architecture and the isolation of cryptographic keys are key factors in the improved security offered by HSMs.
Use in Enterprise-Level Security
In enterprise-level security, HSMs are crucial for safeguarding sensitive data and maintaining regulatory compliance. They are often employed for tasks like secure token generation, encryption, and decryption of sensitive data. Organizations often utilize HSMs for managing and protecting critical assets, such as user credentials and sensitive information. Their implementation contributes significantly to a robust security posture and helps prevent data breaches.
Conclusive Thoughts
In conclusion, prioritizing password security is a proactive measure for maintaining the integrity of your online presence. By understanding and applying the principles Artikeld in this guide, you can significantly reduce the risk of unauthorized access and protect your valuable data. Remember, consistent vigilance and proactive measures are key to securing your digital world.
FAQ Guide
What are some common password security mistakes?
Using easily guessed passwords, reusing passwords across different accounts, and not changing passwords regularly are common mistakes. Failing to enable multi-factor authentication is another significant oversight.
How can I assess the complexity of my password?
Several online tools can assess password strength based on length, character types, and randomness. These tools provide immediate feedback on password robustness.
What is the difference between a weak, medium, and strong password?
Weak passwords are short, simple, and predictable. Medium passwords are slightly more complex but still vulnerable to cracking. Strong passwords are long, random, and use a combination of uppercase and lowercase letters, numbers, and symbols.
How do I recover a forgotten password if I use a password manager?
Password managers typically offer password recovery options through email verification, security questions, or backup codes. Consult your password manager’s documentation for specific recovery procedures.






